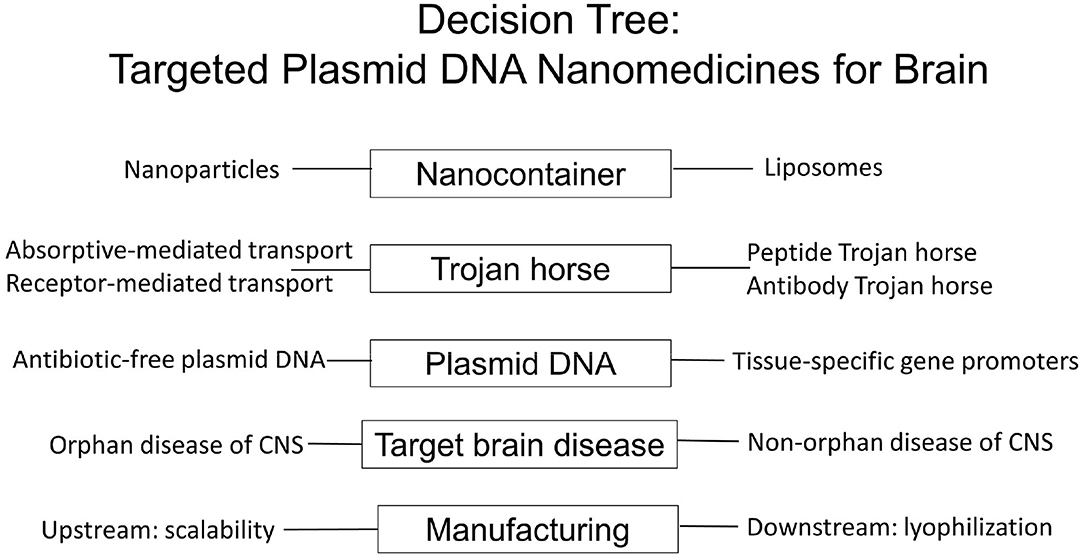
Frontiers | Brain Delivery of Nanomedicines: Trojan Horse Liposomes for Plasmid DNA Gene Therapy of the Brain

Applied Sciences | Free Full-Text | Designing Trojan Detectors in Neural Networks Using Interactive Simulations
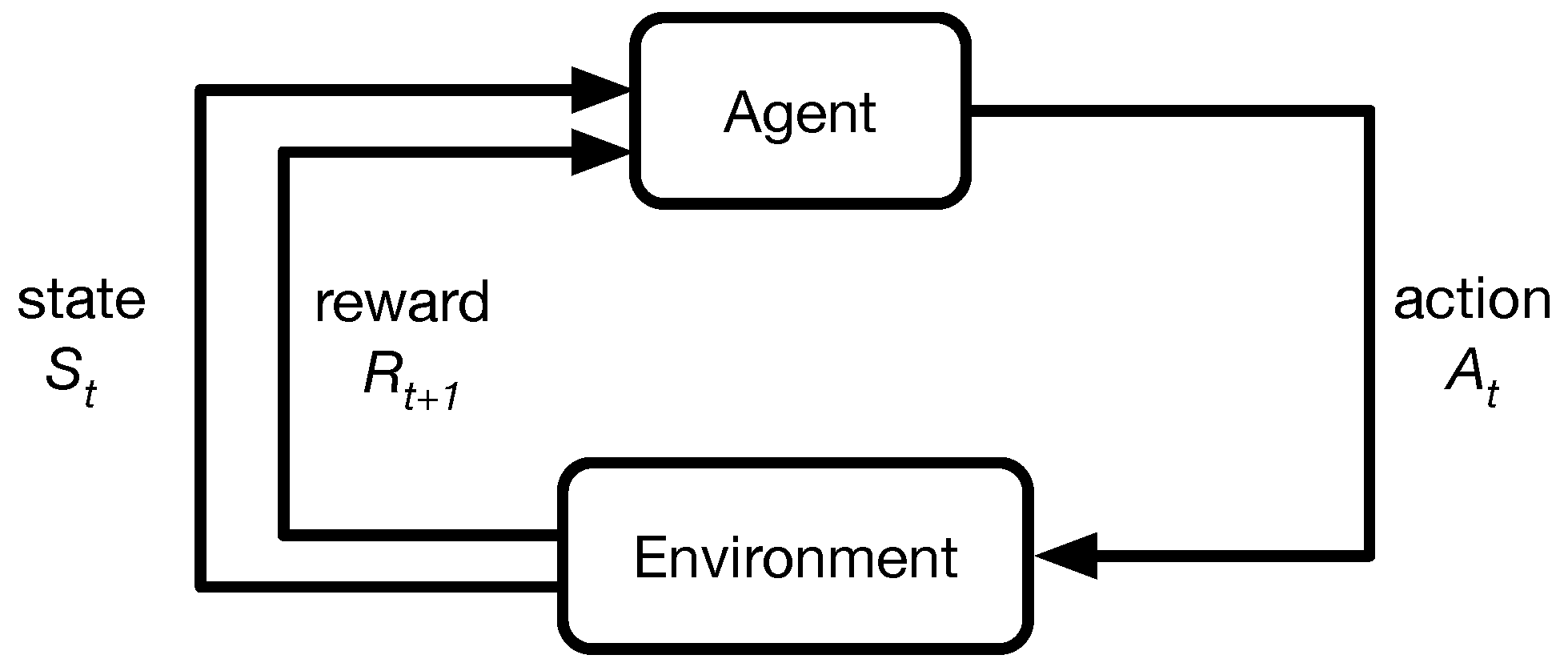
Applied Sciences | Free Full-Text | A Comparison of an Adaptive Self-Guarded Honeypot with Conventional Honeypots
Applied Sciences | Free Full-Text | Evaluation of Local Security Event Management System vs. Standard Antivirus Software

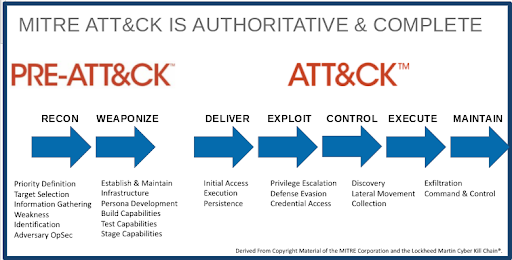
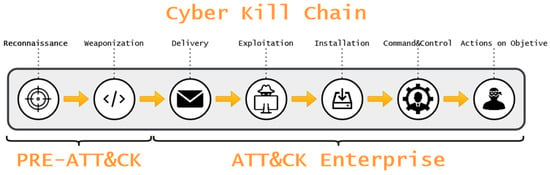
2023 MITRE ATT&CK® Evaluation results: Malwarebytes earns high marks for detection, blocks initial malware executions

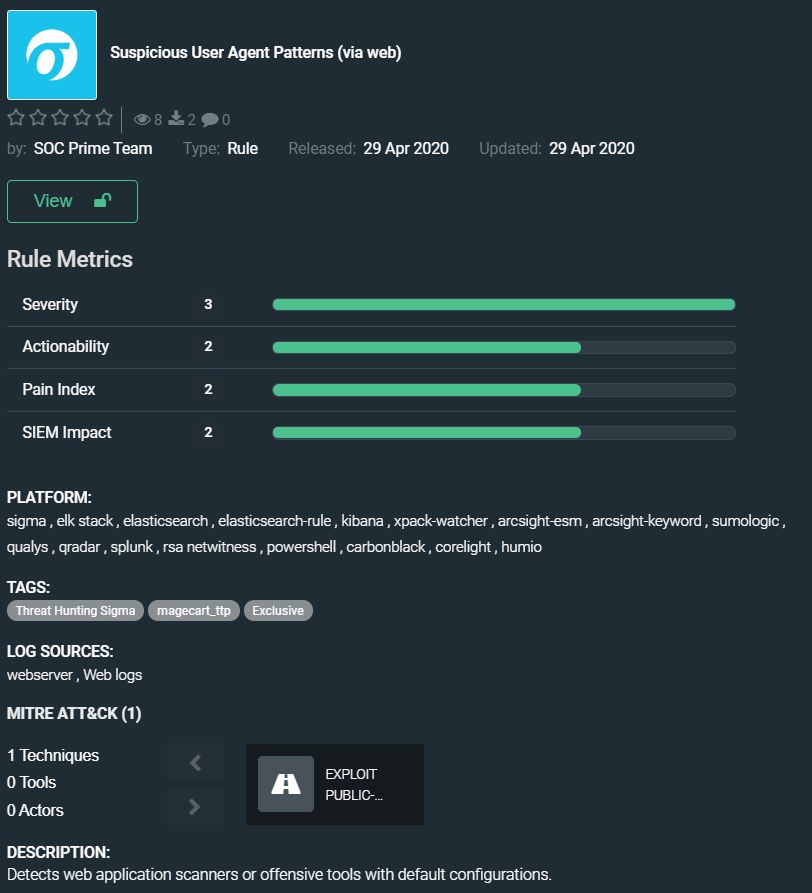
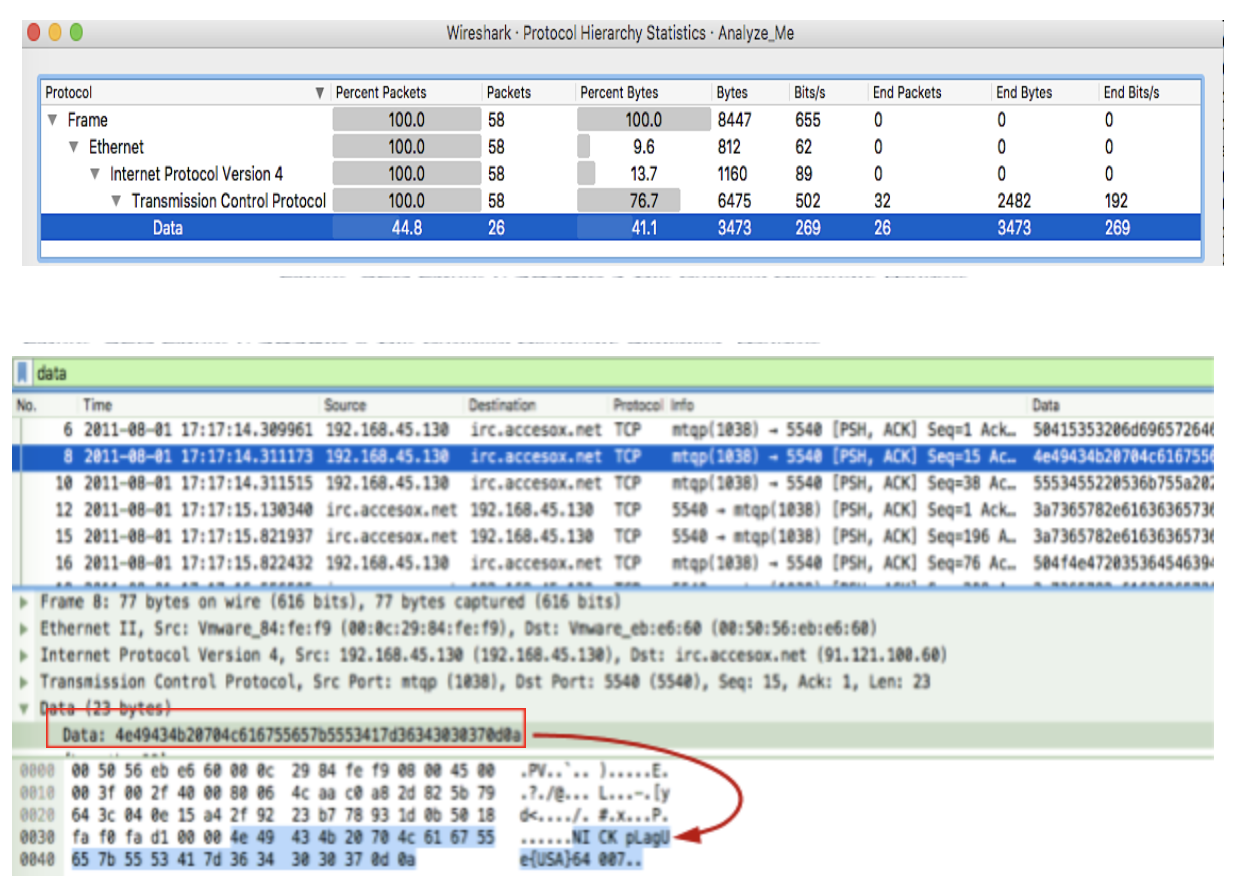
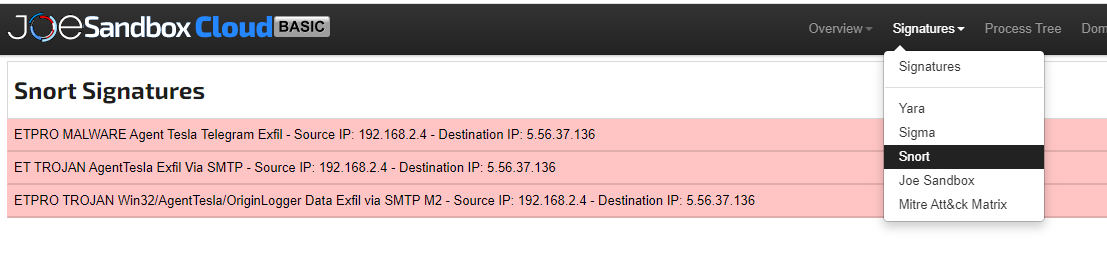
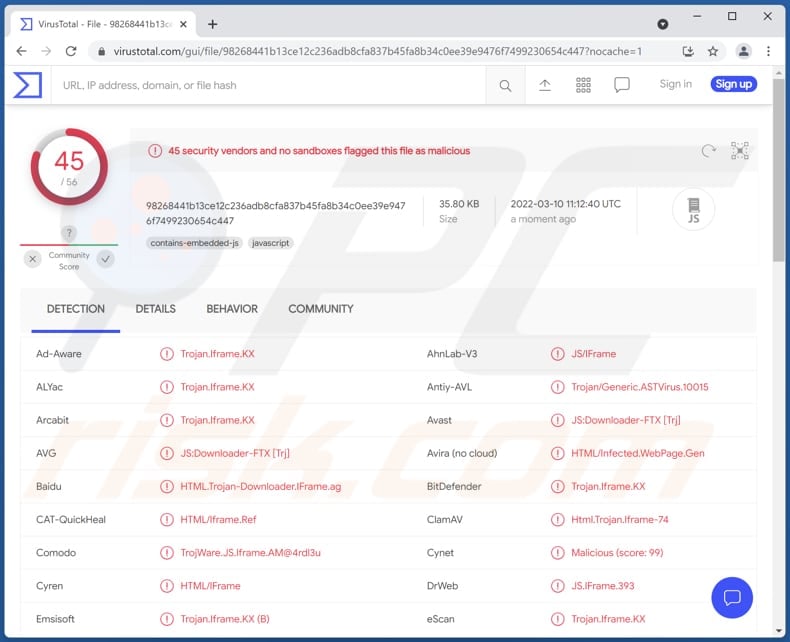
Malware analysis a Malicious Indicator (Trojan.Agent) on my personal machine | by Mohammed Yaseen | Medium

Malware analysis a Malicious Indicator (Trojan.Agent) on my personal machine | by Mohammed Yaseen | Medium